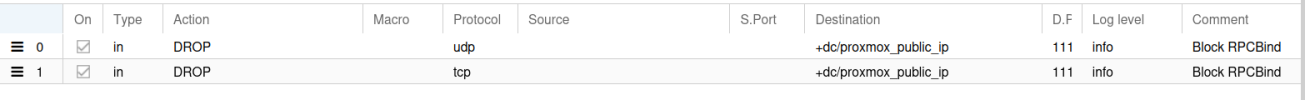
Hi all,
I have an Hetzner ax41 installed with proxmox and ipfire as the router vm. I have additional to the main ip a single ip for the ipfire and a /29 subnet. I can reach the ipfire, but no vm from the subnet. I got a mail from Hetzner abuse, about not allowed MAC addresses.
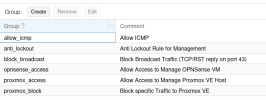
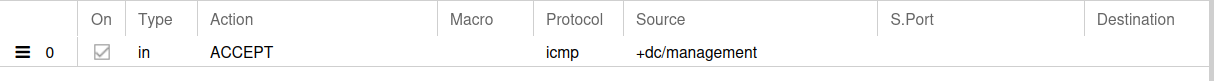
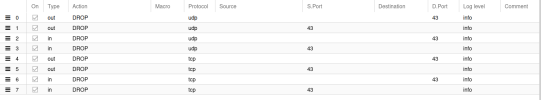
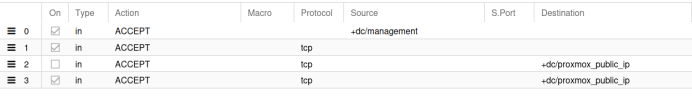
So my network config is:
What is wrong with this config? Why there comming not allowed MAC addresses to the outside?
regards
Bernd
I have an Hetzner ax41 installed with proxmox and ipfire as the router vm. I have additional to the main ip a single ip for the ipfire and a /29 subnet. I can reach the ipfire, but no vm from the subnet. I got a mail from Hetzner abuse, about not allowed MAC addresses.
So my network config is:
Code:
auto lo
iface lo inet loopback
auto enp8s0
iface enp8s0 inet manual
mtu 1500
auto vmbr0
iface vmbr0 inet static
address xxx.yy.131.13/26 # main ip
gateway xxx.yy.131.1
bridge-ports enp8s0
bridge-stp off
bridge-fd 0
mtu 1500
bridge_maxwait 0
up ip addr add ccc.dd.ggg.24/29 dev vmbr0 # subnet
auto vmbr2
iface vmbr2 inet static
address 192.168.1.1/24
ovs_type OVSBridge
ovs_mtu 1500
#green
auto vmbr3
iface vmbr3 inet static
address 192.168.240.1/24
ovs_type OVSBridge
ovs_mtu 1500
#orange
source /etc/network/interfaces.d/*
Code:
ip addr show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr0 state UP group default qlen 1000
link/ether a8:a1:59:37:de:c2 brd ff:ff:ff:ff:ff:ff
3: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether a8:a1:59:37:de:c2 brd ff:ff:ff:ff:ff:ff
inet zzz.vv.rrr.13/26 scope global vmbr0
valid_lft forever preferred_lft forever
inet ccc.dd.ggg.24/29 scope global vmbr0
valid_lft forever preferred_lft forever
inet zzz.vv.rrr.12/26 scope global secondary vmbr0
valid_lft forever preferred_lft forever
inet6 fe80::aaa1:59ff:fe37:dec2/64 scope link
valid_lft forever preferred_lft forever
4: ovs-system: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 62:c6:17:2e:2e:86 brd ff:ff:ff:ff:ff:ff
5: vmbr2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN group default qlen 1000
link/ether be:c1:b6:bd:b6:47 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 scope global vmbr2
valid_lft forever preferred_lft forever
inet6 fe80::bcc1:b6ff:febd:b647/64 scope link
valid_lft forever preferred_lft forever
6: vmbr3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN group default qlen 1000
link/ether a2:20:9a:d3:f5:49 brd ff:ff:ff:ff:ff:ff
inet 192.168.240.1/24 scope global vmbr3
valid_lft forever preferred_lft forever
inet6 fe80::a020:9aff:fed3:f549/64 scope link
valid_lft forever preferred_lft forever
7: tap100i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr0 state UNKNOWN group default qlen 1000
link/ether 5a:a2:a3:26:bb:f8 brd ff:ff:ff:ff:ff:ff
8: tap100i1: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master ovs-system state UNKNOWN group default qlen 1000
link/ether e6:67:7a:5b:89:66 brd ff:ff:ff:ff:ff:ff
9: tap100i2: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master ovs-system state UNKNOWN group default qlen 1000
link/ether 66:21:6f:fc:e1:e3 brd ff:ff:ff:ff:ff:ff
10: tap101i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master ovs-system state UNKNOWN group default qlen 1000
link/ether 06:db:5c:f0:2a:7a brd ff:ff:ff:ff:ff:ff
11: tap101i1: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master ovs-system state UNKNOWN group default qlen 1000
link/ether d2:47:84:a6:b3:85 brd ff:ff:What is wrong with this config? Why there comming not allowed MAC addresses to the outside?
regards
Bernd